DeFi Attacks: Flash Loans and Centralized Price Oracles
DeFi protocols are facing a wave of attacks that use flash loans to target vulnerabilities in smart contracts. The most common exploit relies on centralized price oracles.

DeFi projects are seeing an increasing number attacks using flash loans. Over the past month alone, at least five flash loan attacks have been executed against DeFi protocols (Harvest, Akropolis, Value DeFi, Cheese Bank, and Origin Protocol), and they are increasing in frequency.
The most common variant of this attack is the flash loan-funded price oracle attack. These attacks use flash loans to exploit vulnerabilities in centralized price oracles, manipulate assets' prices, and siphon funds from contracts.
On Monday, Cheese Bank was attacked for $3.3 million, prompting cries from the community to "stop using single source price oracles!"
You have got to be kidding me, another #DeFi protocol just got price oracle attacked for $3.3M in user funds 🤦♂️
— ChainLinkGod.eth (@ChainLinkGod) November 16, 2020
This time it was @CheeseBank2020 using @UniswapProtocol as its sole source of market data
Devs, please stop using single source price oracles!https://t.co/5gtQFUMpfI
So how do flash loans work, and how are they used to exploit vulnerabilities in smart contracts which utilize centralized price oracles? We explore these questions below...
Using Flash Loans to Fund Attacks
How do Flash Loans Work?
Before the invention of flash loans, DeFi-based lending required users to over-collateralize a loan upfront in order to borrow funds. Flash loans introduced a new form of borrowing whereby a user can borrow a large amount of funds without putting up collateral, allowing them to leverage themselves without risking their own funds.
The genius of flash loans is that the borrowed funds must be paid back within the same transaction in which they are borrowed, or else the transaction reverts.
This means that users of flash loans, including attackers, assume very little risk; if the transaction does not "break even" and the loan cannot be paid back, the whole thing reverts, meaning the user loses nothing more than the cost of gas. In contrast, the potential returns are considerable.
Why are Flash Loans Used in Attacks?
Flash loans are often used non-maliciously to take advantage of arbitrage opportunities across different exchanges - but recently, flash loans have been increasingly used in attacks on DeFi protocols.
It should be noted that most of these attacks do not require flash loans, and can in fact be executed by anyone with enough capital (i.e. a whale). All flash loans do is allow anyone "to act like a whale for the duration of a tx."
Like clockwork, each time a flashloan is used in this kind of event we got the grumpy old man yelling at clouds.
— Marc Zeller (@lemiscate) October 26, 2020
Flash loans are a tool they allow you to act like a whale for the duration of a tx.
what happened today was accessible to anyone with 50M$
or much less and more txs
However, flash loans do make attacks more viable for several reasons:
- Zero Upfront Capital - Flash loans increase the number of people who can conduct an attack - rather than just whales, they open the opportunity up to anyone with the technical ability, regardless of their financial standing.
- Less Capital at Risk - Even for a well-funded attacker, it makes more sense to use a flash loan rather than their own funds. This is because if the attack were to fail for any reason, the transaction reverts, meaning the attacker loses nothing except gas costs.
Despite these factors, it should be recognized that flash loans are simply a tool - and in most cases, the real culprit is not flash loans, but vulnerabilities in smart contracts. If smart contracts were built more robustly, flash loan attacks would not be possible.
Price Oracle Attacks
As mentioned above, the most common attack to make use of flash loans is the price oracle attack.
In such events, attackers essentially create artificial arbitrage opportunities by instantaneously borrowing, swapping, depositing, and again borrowing large numbers of tokens. This action exploits a vulnerability in certain price oracles, which leads to a target token's price being artificially moved on a single exchange; a disparity which can then be arbitraged.
While flash loans may seem like the dangerous component here, these attacks would not be possible without another component adopted by many DeFi protocols: centralized price oracles.
What are Centralized Price Oracles?
For the uninitiated, price oracles are third-party services that allow smart contracts to receive external price data from outside of their ecosystem. To mitigate the risk of manipulation, projects such as Chainlink offer decentralized price oracles.
However, rather than using decentralized solutions, many DeFi protocols have opted instead to use centralized price oracles. These feeds draw prices directly from asset pairs on a single decentralized exchange (DEX).
How are Centralized Price Oracles Used in Attacks?
If a DeFi protocol relies on price data from a single DEX, any changes in that DEX's price data - whether representative of the actual market price or not - are considered true and accurate by the protocol's smart contracts.
As such, if an attacker can manipulate the price of an asset on that single DEX, this leads to inaccurate price data being fed to all protocols which rely on that DEX as a price oracle, making them vulnerable to exploitation. Flash loans make it easy to manipulate price data on a single DEX.
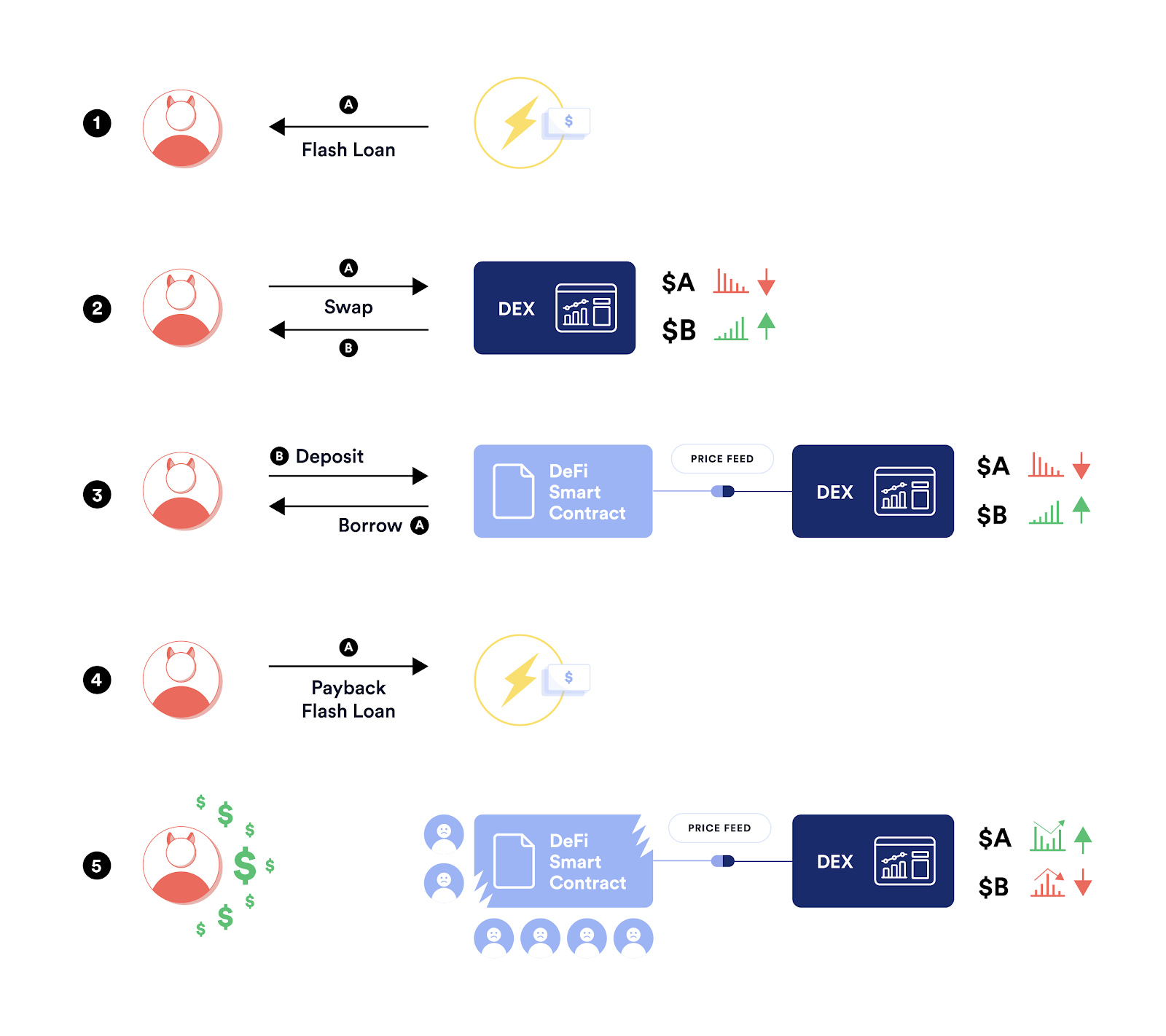
Once an attacker has manipulated the price of an asset on the target DEX, they can then "trick" the protocol which relies on its price feed into allowing the sale or purchase of assets at above or below market price, at the expense of regular users.
Quick Side Note: Other Flash Loan Attacks
While price oracle attacks are the most common malicious application of flash loans, they are not the only one. Flash loans may also be used to exploit other vulnerabilities in smart contracts.
For example, on Tuesday - less than 24 hours after Cheese Bank was attacked - stablecoin project Origin Protocol was attacked for $7 million of user funds. This attack did not rely on a centralized price oracle, but rather a vulnerability in Origin's rebasing mechanism.
Another one bites the dust: Origin Dollar (OUSD) exploited for $2.25m in DAI and $1m in Ethereum.
— Nick C. (@n2ckchong) November 17, 2020
Flash loan attacker/exploiter is already washing the funds via RenBTC. pic.twitter.com/3VouT7AiJe
Price oracle attacks, however, are still the most common malicious use of flash loans at this stage.
How the Price Oracle Attack Works
To examine more deeply how flash loan-funded price oracle attacks work, we can look at the recent attack on Cheese Bank.
The basic structure of the attack can be seen in the flow of the transaction which executed it:
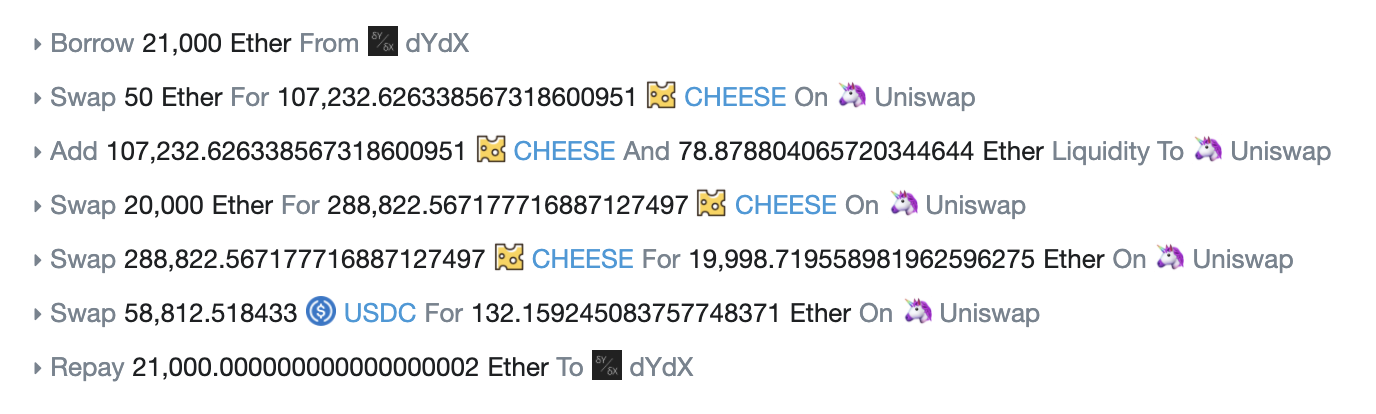
Looking at the details of the transaction, we can delve further into how a flash loan-funded price oracle attack is structured. Blockchain security firm PeckShield published an analysis of the Cheese Bank incident, and identified several steps to the attack:
Step 1: Flash Loan
- Take a flash loan of 21k ETH from dYdX.
Step 2: Buy CHEESE
- Swap 50 ETH to 107k CHEESE on Uniswap.
Step 3: Deposit CHEESE and ETH on Uniswap
- Add 107k CHEESE and corresponding 78 ETH into the liquidity pool on Uniswap.
- Receive CHEESE/ETH Uniswap LP tokens in return.
Step 4: Use LP tokens to Mint sUSD tokens
- Mint sUSD_V2 tokens with all LP tokens acquired via Step 3.
- This allows the exploit contract to use those LP tokens as collaterals for borrowing crypto assets from Cheese Bank.
Step 5: Artificially inflate the price of CHEESE on Uniswap
- Raise the CHEESE price on Uniswap by swapping 20k ETH to 288k CHEESE, which makes the UNI LP tokens more valuable as collateral in Cheese Bank.
- This is the crucial step in this incident, since Cheese Bank uses the amount of WETH in a liquidity pool to estimate the price of the corresponding LP token.
- The unit price of the Uniswap CHEESE/ETH LP token is computed as the total value divided by the total supply of LP tokens. Because the attacker has increased the amount of WETH in the pool (by adding liquidity with ETH from the flash loan), the price of the LP token increases according to the Cheese Bank oracle.
Step 6: Refresh the price feeds of Cheese Bank
- Invoke the Cheese Bank price oracle's
refresh()function to refresh the price of the Uniswap CHEESE/ETH LP token (which is derived from the amount of WETH in the liquidity pool, and the ETH price derived from the Uniswap USDT/ETH pool).
Step 7: Drain funds from Cheese Bank
- The manipulated Uniswap CHEESE/ETH pool (with 20k+ WETH) allows the bad actor to drain all the USDC, USDT, and DAI held in Cheese Bank by legitimate
borrow()calls to Cheese Bank's contract. - In the case of this attack, this equates to 2m USDC, 1.23m USDT and 87k DAI.
Step 8: Swap funds into ETH to pay back the flash loan
- Swap 288k CHEESE back to 19.98k ETH on Uniswap.
- Swap 58k USDC to 132 ETH on Uniswap.
- Collect the hacked assets into a single address: 0x02b7.
Step 9: Pay back the flash loan
- Return the 21k ETH to dYdX to pay back the flash loan.
Conclusions
By using an AMM-based centralized price oracle, Cheese Bank opened itself up to this kind of attack - which, again, could have been executed by anyone with sufficient capital, but was made easier through the availability of flash loans.
This string of attacks highlights the importance of DeFi protocols using decentralized price oracles. Especially now that this vulnerability has been widely publicized, a failure to migrate to a decentralized oracle such as Chainlink could be catastrophic for the protocols that still rely on a single DEX for their price data.

- Follow us and reach out on Twitter
- Join our Telegram channel
- For on–chain metrics and activity graphs, visit Glassnode Studio
- For automated alerts on core on–chain metrics and activity on exchanges, visit our Glassnode Alerts Twitter
